Uks ms resumes online orders following cyber incident – UK’s MS resumes online orders following a cyber incident, a critical moment demanding careful consideration of the fallout and recovery strategies. This incident likely disrupted online ordering systems, affecting order processing, payment, and customer communication. Potential consequences range from delays and cancellations to data breaches and reputational damage. Understanding the impact, response strategies, and security measures is crucial for both the company and its customers.
The company’s swift return to online operations highlights their commitment to customer service and business continuity. This involves not only restoring online order processing but also actively communicating with customers during and after the incident. Effective communication, clear FAQs, and dedicated support channels are vital in managing customer inquiries and maintaining trust. The incident also serves as an opportunity to review and strengthen security protocols to prevent future attacks, and to implement robust business continuity plans.
The incident demands a deep dive into security measures, including data encryption, multi-factor authentication, and regular audits, ensuring that the company is prepared to face similar challenges in the future.
Impact of the Cyber Incident on Online Orders
A cyber incident targeting a UK-based online medical supplies company (MS) can severely disrupt its online ordering operations. The repercussions extend far beyond the technical realm, affecting customer trust, operational efficiency, and the company’s reputation. This analysis explores the potential impacts of such an event on online order fulfillment and the associated consequences.
Potential Disruptions to Online Ordering Systems, Uks ms resumes online orders following cyber incident
A cyberattack can lead to a cascade of disruptions across the entire online ordering process. This may include system outages, hindering order placement and processing. Payment systems might be compromised, leading to difficulties in completing transactions securely. Communication channels with customers, such as email and chat support, could also be affected, impacting their ability to receive updates and support.
The severity of these disruptions depends on the nature and scope of the attack.
Following the UK’s MS’s resumption of online orders after the cyber incident, it’s fascinating to see how other sectors are reacting. For example, Church England is planning a substantial £22 billion spending spree, apparently fueled by signs of a revival, as detailed in this article church england plans record 22 bln spend after signs revival. While the religious sector’s financial outlook is positive, the UK’s MS’s focus remains on ensuring smooth online operations and customer confidence after the recent cyber incident.
Impact on Order Fulfillment
The cyber incident could lead to delays in order processing. Orders might be held up indefinitely, creating frustration and inconvenience for customers. Inventory management systems could be compromised, making it difficult to track stock levels and fulfill orders accurately. The company may experience shortages or be unable to deliver certain items, especially if the attack affects supply chain logistics.
Disruptions in order fulfillment are common in cases of cyberattacks, and can have a significant impact on customer satisfaction.
Impact on Payment Systems
Payment systems are critical to online ordering, and a cyberattack can jeopardize this process. Compromised payment gateways can lead to fraudulent transactions, customer data breaches, and the inability to process legitimate payments. The company may need to temporarily suspend online payments, impacting revenue and customer experience. Protecting payment data and ensuring secure transaction processing are vital to maintaining trust and preventing financial losses.
Consider the 2017 Equifax breach as a case study; such events can severely damage customer confidence and financial stability.
Impact on Customer Communication
Communication with customers is essential during a cyber incident. Interruptions in email, chat support, and phone lines can leave customers in the dark about their order status and the company’s response. The lack of clear communication can cause confusion, anxiety, and dissatisfaction, potentially leading to negative reviews and reputational damage. Maintaining open communication channels and providing regular updates are critical for mitigating customer concerns.
Possible Consequences for Customers
Customers face various potential consequences, depending on the severity of the incident. These range from order delays to complete cancellations. Data breaches expose customer information to risk, potentially leading to identity theft or financial fraud. Customers who experience issues with their orders or data breaches will be understandably upset and may consider switching to competitors. The potential for harm to customers is significant.
Potential Reputational Damage for the MS Company
A cyber incident can severely damage a company’s reputation, particularly in the medical supplies sector where trust is paramount. Negative publicity, diminished customer confidence, and decreased sales are likely consequences. Customers may be hesitant to use the company’s services again, and the company’s credibility could be significantly impacted. Reputation damage can be long-lasting and costly to repair.
UK’s MS resumes online orders following a recent cyber incident, but the fallout continues. While the immediate crisis is hopefully behind them, it’s interesting to note the parallel with fundraising efforts from prominent figures like Cory Booker and Alexandria Ocasio-Cortez, who are raising significant funds for various causes, particularly in the face of challenging political landscapes.
The challenges of rebuilding trust and online systems are undeniably similar to those faced in the political sphere, and it remains to be seen how these issues will be navigated in the coming months.
Comparison of Order Disruption Scenarios
| Scenario | Description | Impact on Customers | Impact on Company |
|---|---|---|---|
| Partial Disruption | Certain parts of the online ordering system are affected. | Some delays in order processing and communication. | Reduced efficiency and potential loss of revenue. |
| Complete Shutdown | Entire online ordering system is unavailable. | Orders cannot be placed or tracked. | Significant loss of revenue and potential customer churn. |
| Data Breach | Customer data is compromised. | Risk of identity theft and financial fraud. | Significant reputational damage and potential legal liabilities. |
Response Strategies for Maintaining Online Operations
Navigating a cyber incident that disrupts online order fulfillment requires a swift and strategic response. A robust incident response plan, coupled with clear communication channels and customer-centric strategies, can minimize the impact and ensure a smooth recovery. This crucial period demands a proactive approach, aiming to restore operations as quickly as possible while maintaining customer trust and satisfaction.Effective mitigation strategies are vital to limit the fallout from a cyber incident.
These strategies should encompass various aspects of online order fulfillment, from order processing to customer service. Implementing these measures promptly and efficiently is key to minimizing downtime and preserving business continuity.
Mitigating the Impact on Order Fulfillment
To limit the disruption to online order fulfillment, businesses should deploy several strategies. These strategies should focus on quickly identifying the extent of the damage and implementing immediate countermeasures. These actions include prioritizing essential tasks, allocating resources effectively, and utilizing backup systems. For instance, temporarily shifting to a secondary data center can minimize the impact of the attack and maintain essential operations.
Alternative fulfillment methods, such as utilizing a third-party fulfillment service or manually processing orders, can also be explored.
Restoring Online Order Processing and Customer Service Channels
Restoring online order processing and customer service channels requires a phased approach. First, identify the specific systems affected and prioritize their restoration. Secondly, ensure the availability of necessary resources, such as personnel and technical support. Finally, implement rigorous testing procedures to verify the restored systems’ functionality before fully releasing them to users. A meticulous recovery plan is essential to avoid future issues and guarantee a swift return to normalcy.
For example, a company might initially restore order placement, then gradually reinstate other functions like order tracking and customer support.
Importance of Customer Communication
Maintaining open communication with customers during and after the incident is paramount. This transparency builds trust and mitigates potential damage to the company’s reputation. Providing timely updates, addressing concerns promptly, and offering support channels are crucial components of this strategy. This demonstrates a commitment to customer well-being, and it can significantly influence customer loyalty and satisfaction. For instance, a clear and consistent communication strategy can help alleviate anxieties and maintain customer trust.
Need for a Robust Incident Response Plan
A well-defined incident response plan is critical for effectively handling cyber incidents. This plan should Artikel specific procedures for identifying, containing, and recovering from such events. It should also include roles and responsibilities for personnel involved in the response. Having a documented plan allows for a structured approach, ensuring that everyone involved knows their responsibilities and actions during a crisis.
This plan acts as a roadmap for navigating the complex and dynamic situation, minimizing the negative impact and maximizing recovery efficiency.
Communication Channels for Customer Updates
Clear and accessible communication channels are essential to keep customers informed. This transparency builds trust and reduces uncertainty. Utilizing various channels allows for broader reach and ensures that customers receive updates via their preferred method.
| Communication Channel | Description | Pros | Cons |
|---|---|---|---|
| Direct communication to individual customer inboxes | Targeted communication; detailed information | Potential for spam filters; may not be immediately seen | |
| SMS/Text Messages | Short, concise updates delivered via mobile | High visibility; quick updates | Limited space for detail; not ideal for complex information |
| Website Announcement | Public notice on company website | Accessible to all customers; easily updated | May not reach all customers; requires immediate action |
| Social Media | Broad reach; direct engagement with customers | Real-time updates; direct feedback | Potential for negative feedback; requires constant monitoring |
| Dedicated Hotline | Phone line for customer inquiries | Immediate assistance; personalized support | High call volume; limited capacity |
Security Measures for Preventing Future Incidents
The recent cyber incident significantly impacted our online order systems. Moving forward, robust security measures are paramount to prevent similar breaches and maintain customer trust. This section Artikels critical security practices for strengthening our online order systems and mitigating future threats.Implementing these strategies will not only protect our systems but also demonstrate our commitment to data security and responsible online operations.
This proactive approach is essential to building a resilient infrastructure capable of handling evolving cyber threats.
Best Practices for Strengthening Online Order Systems
Strengthening online order systems against cyber threats requires a multi-faceted approach. This involves implementing comprehensive security protocols, regularly assessing vulnerabilities, and employing user authentication strategies. Prioritizing data security and user experience will ensure the ongoing integrity and efficiency of our online operations.
UK’s MS resumes online orders following the cyber incident, a welcome relief for customers. While we’re happy to see things moving forward, it got me thinking about the fascinating world of horse racing, and specifically, the top 10 racehorses of all time according to AI. This list is certainly intriguing, and I’m sure it’s also fascinating to consider how AI might be applied to other business issues, even those related to the incident at MS.
Hopefully, the resumption of online services will be smooth and efficient, minimizing any further disruptions.
- Employing strong, regularly updated passwords is a fundamental security measure. Users should be educated on creating and maintaining complex passwords that combine upper and lower case letters, numbers, and symbols.
- Implementing multi-factor authentication (MFA) is crucial to enhance security. MFA adds an extra layer of verification beyond a simple password, making it significantly harder for unauthorized access.
- Regularly updating software and applications is essential to address security vulnerabilities. Outdated software often contains known weaknesses that attackers can exploit.
- Educating employees and customers about phishing and social engineering attacks is paramount. Understanding these tactics empowers individuals to identify and avoid fraudulent attempts.
Importance of Robust Security Protocols and Data Encryption
Robust security protocols are vital for protecting sensitive customer data and maintaining the integrity of online transactions. Data encryption is an essential component of these protocols, ensuring that sensitive information remains confidential.
- Data encryption should be implemented for all sensitive data, including customer credit card information, addresses, and personal details. This ensures that even if data is intercepted, it remains unreadable without the decryption key.
- Employing encryption protocols like SSL/TLS for all online transactions safeguards data during transmission. This prevents eavesdropping and ensures the security of financial information exchanged between customers and our servers.
- Regularly review and update security protocols to reflect emerging threats. This includes staying informed about the latest vulnerabilities and adapting our protocols accordingly.
Need for Regular Security Audits and Vulnerability Assessments
Proactive security audits and vulnerability assessments are essential for identifying potential weaknesses in our online order systems. Regular assessments help us stay ahead of emerging threats and prevent costly breaches.
- Conducting regular security audits of the online order system will uncover potential vulnerabilities and weaknesses. These audits should include a thorough examination of all security measures in place, from access controls to data encryption.
- Implementing vulnerability assessments helps pinpoint specific weaknesses in our systems. These assessments utilize automated tools and manual checks to identify potential points of entry for attackers.
- Results from these audits and assessments should be analyzed to prioritize remediation efforts. Prioritization ensures that the most critical vulnerabilities are addressed first.
Implementation of Multi-Factor Authentication
Multi-factor authentication (MFA) is a critical security measure that adds an extra layer of security beyond passwords. This approach requires multiple forms of verification, significantly reducing the risk of unauthorized access.
- Implementing MFA across all user accounts enhances security by requiring additional verification steps beyond a password. This can include security questions, one-time codes, or biometric authentication.
- MFA is especially important for privileged accounts, such as administrator accounts. Restricting access to these accounts with MFA significantly reduces the impact of compromised credentials.
- Training users on the use of MFA will ensure smooth and efficient implementation.
Categorization of Security Measures
The following table categorizes security measures by their impact on the online order process.
| Category | Description | Examples |
|---|---|---|
| Technical | Measures related to the technology infrastructure. | Data encryption, firewall configuration, intrusion detection systems |
| Procedural | Measures related to the processes and workflows. | Regular security audits, incident response plans, employee training |
| Managerial | Measures related to the organizational structure and management. | Security policies, risk assessments, budget allocation for security |
Customer Service and Support During the Incident
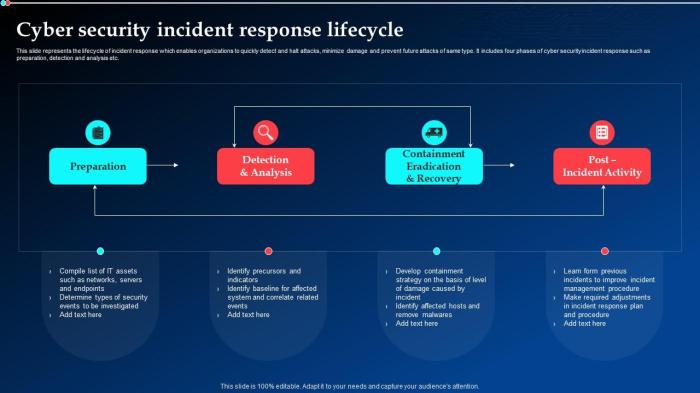
Navigating a cyber incident requires a robust customer service strategy. Effective communication and support during such disruptions are crucial for maintaining customer trust and minimizing the long-term impact. Customers expect prompt responses, clear explanations, and reassurance that their concerns are being addressed. A well-structured support system, designed with empathy and patience in mind, can significantly mitigate the fallout.Addressing customer inquiries and concerns swiftly and professionally is paramount during a cyber incident.
Failure to do so can lead to negative publicity, loss of customer loyalty, and reputational damage. By proactively addressing issues and providing clear information, businesses can demonstrate their commitment to customer satisfaction, even in challenging circumstances.
Importance of Clear and Consistent Communication
Clear and consistent communication regarding the incident and its impact is vital. Customers need to understand what happened, how it affects them, and what steps are being taken to resolve the issue. Ambiguity or conflicting messages can escalate anxiety and frustration, making the situation worse. A transparent communication plan ensures that all stakeholders, including customers, employees, and the public, are kept informed of the situation’s progress.
A unified message, delivered through various channels, fosters trust and confidence.
Strategies for Managing Customer Inquiries and Complaints
Effective strategies for managing customer inquiries and complaints include establishing dedicated support channels, pre-emptively addressing common questions, and actively monitoring feedback. Utilizing multiple communication channels, such as email, phone, and online chat, ensures accessibility for all customers. A dedicated support line or email address for incident-related inquiries ensures swift responses. An FAQ page, proactively addressing common questions and concerns, can reduce the workload on customer support teams and provide immediate answers to frequently asked questions.
Methods for Providing Support
Providing various support methods ensures that customers can access help through their preferred channels. A well-structured support system incorporates different channels, offering flexibility and convenience. This multifaceted approach caters to diverse customer needs and preferences.
| Support Method | Description | Example |
|---|---|---|
| FAQs | Frequently Asked Questions page on the website. | “What is the status of my order?” or “How will my order be affected?” |
| Dedicated Support Lines | Phone numbers for customers to call for immediate assistance. | A toll-free number specifically for the incident. |
| Online Chat | Live chat functionality on the website for instant support. | Real-time assistance through chat, providing instant answers. |
| Email Support | Dedicated email address for incident-related inquiries. | An email address to receive and respond to customer emails related to the incident. |
Empathy and Patience in Dealing with Affected Customers
Demonstrating empathy and patience is crucial in handling affected customers. Acknowledging their frustration and concerns, even in a difficult situation, fosters a sense of understanding and trust. Providing helpful and reassuring information, actively listening to their concerns, and addressing their issues with a sense of urgency builds rapport and improves the overall customer experience. A personal touch in the communication, even in a standardized response, can significantly enhance customer satisfaction.
Legal and Regulatory Considerations: Uks Ms Resumes Online Orders Following Cyber Incident
Navigating the digital landscape requires a keen understanding of the legal and regulatory frameworks governing cyber incidents, particularly for businesses operating in the UK. This section delves into the crucial legal aspects of handling a cyber incident, focusing on the obligations of a UK-based online retailer like us, and the potential consequences of non-compliance.The UK boasts a robust regulatory environment designed to protect individuals and businesses from the detrimental effects of cybercrime.
Understanding and adhering to these regulations is paramount to minimizing potential legal ramifications and maintaining the trust of our customers.
Relevant Legal and Regulatory Frameworks
UK law provides a comprehensive framework for handling cyber incidents. Key legislation includes the Data Protection Act 2018 (DPA 2018), the Information Security Breach Notification Regulations (ISB 2018), and the UK’s broader criminal justice system for offences related to data breaches and cyberattacks. These regulations form the cornerstone of our legal obligations in the aftermath of a cyber incident.
Reporting Obligations to Relevant Authorities
Prompt and accurate reporting to relevant authorities is critical following a cyber incident. This involves notifying the Information Commissioner’s Office (ICO) if a data breach occurs, potentially impacting 250 or more individuals, as stipulated by the DPA 2018 and the ISB 2018. The specific reporting procedures and deadlines are Artikeld in the regulations. Failure to comply with these obligations can lead to significant penalties.
Potential Legal Ramifications for Non-Compliance
Non-compliance with data protection and reporting regulations can result in substantial legal repercussions. Penalties can include significant financial fines, reputational damage, and even criminal prosecution, depending on the severity and nature of the breach. This is crucial to understand to drive proactive security measures and establish robust incident response plans. Examples include the fines levied against companies for data breaches in other jurisdictions, which demonstrate the severity of these regulations.
Data Protection Laws and Customer Data Security
Protecting customer data is a fundamental legal and ethical obligation. The DPA 2018 Artikels strict rules for processing and storing personal data, including the requirement for appropriate security measures to prevent unauthorized access, use, disclosure, alteration, or destruction. Failure to implement these measures can result in legal action and significant financial penalties. The company’s commitment to safeguarding customer data is paramount to maintaining trust and avoiding potential legal disputes.
Summary of Key Legal and Regulatory Aspects for Online Order Systems in the UK
| Legal/Regulatory Aspect | Description | Impact on Online Orders |
|---|---|---|
| Data Protection Act 2018 (DPA 2018) | Governs the processing and storage of personal data. | Requires robust security measures to protect customer data during order processing. |
| Information Security Breach Notification Regulations (ISB 2018) | Artikels reporting procedures for data breaches. | Obligates us to notify relevant authorities in case of a significant breach. |
| Criminal Justice System | Addresses criminal offences related to data breaches. | Possible prosecution for intentional breaches or reckless negligence. |
| General Data Protection Regulation (GDPR) | European regulation that applies to data transfers outside of the EU. | Applicable if international transfers of customer data are involved. |
Business Continuity Planning for Online Operations
A robust business continuity plan is crucial for online operations, especially in the face of unforeseen disruptions like cyber incidents. A well-structured plan ensures minimal operational downtime and allows businesses to swiftly adapt and recover. This is not just about surviving an incident, but about maintaining customer trust and demonstrating resilience in the digital age.Having a comprehensive business continuity plan minimizes the impact of disruptions and safeguards the future of online order processing.
This proactive approach helps businesses maintain customer confidence and operational efficiency. It’s about preparedness, not just reaction.
Importance of Backup Systems and Alternative Channels
Backup systems and alternative channels are vital components of a robust business continuity plan. They provide a failsafe mechanism to maintain operations during disruptions. A crucial aspect of this plan is identifying and utilizing redundant systems, such as geographically dispersed servers or cloud-based backups. This ensures business continuity even when primary systems are unavailable. The availability of alternative channels, like phone support or email communication, ensures continued customer engagement.
This also extends to alternative payment gateways and shipping options.
Strategies for Minimizing Disruption
Implementing strategies to minimize disruption requires a proactive approach. Proactive monitoring of systems and networks is essential to identify potential vulnerabilities and address them before they escalate into major issues. Developing a rapid response protocol ensures a swift and organized reaction to incidents. Regular testing of backup systems and alternative channels is vital to verify their efficacy and identify any necessary improvements.
Contingency Plans for Online Order Processing
Effective contingency plans are essential for various aspects of online order processing. These plans need to address different potential disruptions and their varying impacts. The table below illustrates potential contingency plans for different impact areas:
| Impact Area | Contingency Plan | Description |
|---|---|---|
| System Failure | Redundant Server Deployment | Deploying a secondary server in a different geographical location to ensure continued operation in case of a primary server failure. This reduces single point of failure risk. |
| Network Outage | Alternative Communication Channels | Implementing alternative communication channels, such as email, phone support, or social media, to maintain customer communication during network outages. This includes notifying customers of the outage and estimated restoration time. |
| Payment Gateway Issue | Temporary Manual Processing | Establishing a temporary manual payment processing system in case of a payment gateway failure. This involves alternative payment options like direct bank transfers or secure third-party payment processors. |
| Shipping Delays | Alternative Shipping Providers | Identify and pre-qualify alternative shipping providers to ensure continued order fulfillment in case of delays or disruptions with primary providers. This might involve utilizing different shipping carriers for different order categories or geographical locations. |
| Cyberattack | Data Recovery Procedures | Establish and regularly test data recovery procedures for quick restoration in case of a cyberattack. This includes establishing backup copies of data and developing a clear recovery strategy. |
Final Thoughts
In conclusion, the UK’s MS’s resumption of online orders after the cyber incident underscores the importance of swift response, proactive communication, and robust security measures. This incident highlights the need for detailed business continuity planning, comprehensive incident response strategies, and unwavering customer support during times of disruption. The company’s approach to recovery sets a precedent for other businesses facing similar challenges, emphasizing the importance of learning from such incidents and strengthening resilience against future threats.